Consumer intelligence
What is SOCMINT? Definitions, tools, and tips
Learn how social media intelligence uses public data to support security, cyber defense, crisis response, and disinformation detection.
January 13, 2026
There are approximately 5.4 billion social media users as of 2025. For comparison, there are approximately 6 billion people over the age of 15 in the entire world. In other words, almost all adults (and most teenagers) are using social media.
And they’re using it a lot. An average of 141 minutes a day in 2025, down from a peak of 151 minutes in 2023.
During the 857 hours they spend on social media every year, people post a lot of personal information. They share locations. And their interactions reveal likes, preferences, connections, and potential future behaviors. All of that information creates a robust data set for social media intelligence.
People often focus on the value of this information for marketers. All these data signals are certainly useful for targeting people with the right products at the right time.
But there’s also information to mine here that can help keep populations safe by:
predicting digital and real-world threats,
flagging disinformation campaigns by bad actors
and bolstering cyber defense.
Social media intelligence (aka SOCMINT or SMI) relies on publicly available information. There's no hacking or espionage involved, but the intelligence is still very valuable. The idea is to analyze big data trends and public content in a legal way that respects individual users’ privacy.
What is SOCMINT?
SOCMINT is the practice of using public data from social media platforms to generate insights that support:
public safety,
national security,
law enforcement,
public policy decisions,
and election integrity.
(Note: SOCMINT can also be used to support marketing objectives. Learn how marketers can use SOCMINT in our post on the Hootsuite Blog.)
Who can collect social media intelligence — and why?
Realistically, anyone can collect social media intelligence. Remember, SOCMINT relies on public data. By definition, that means the data is out there for anyone to see.
Rather than who can collect SOCMINT, the more important question is who would want to collect SOCMINT. Here are some main groups that can benefit from SOCMINT tools.
Governments, intelligence & security agencies, and law enforcement. To detect public safety threats, criminal activity, foreign influence campaigns, and even potential terrorist activities.
Cybersecurity specialists. To identify data breaches, leaks, and cyberespionage threats.
Later in this post we’ll talk about some of the rules these groups must follow to ensure they use SOCMINT legally and ethically.
What kind of social media data can be collected?
As we’ve already said, there is a lot of information out there that’s open to the public and accessible by anyone.
The vast amount of data people share on social media is one reason lawmakers around the world have concerns about TikTok. They reveal more than they may realize, both through the content they post and through the ways they interact with other content.
Here are some of the types of social media data to collect through SOCMINT:
Individual demographic data from public profiles. Employment details, hometown, education, gender, relationship status, etc.
Location and geotag information for individuals and visual content
Connections and interactions between individuals and groups (social network mapping)
Opinions, ideas, and real-time updates expressed in public social media posts, comments
Image and video data of situations in progress
Top posters and opinion leaders on a topic
Aggregate data on conversation themes, connections between topics, and public opinion (opinion mapping)
Aggregate demographic and location data of people who engage on specific topics or with specific types of content
SOCMINT vs. OSINT: What’s the difference?
SOCMINT is a component of OSINT, or open-source intelligence. The difference is that open-source intelligence includes all public data sources. This includes newspapers, company records, and so on.
SOCMINT focuses exclusively on information sourced from social platforms. Facebook, Instagram, X, Reddit, TikTok, and so on. SOCMINT is generally easier to find and analyze, especially when you’re using the right tools.
The role of SOCMINT in modern intelligence and security
Counterterrorism and threat detection
Intelligence agencies have always used “chatter” to watch for threats. Social media provides a much larger dataset to monitor and analyze. For example, counterterrorism agencies can monitor social platforms for:
extremist propaganda and ideology,
attempts to recruit or radicalize,
and discussions of how to commit violence.
SOCMINT tools can also help identify less obvious threats, or threats that are in the very early stages. These may be signalled by complaints against specific groups, general dissatisfaction with social norms, and so on, especially if they start to escalate.
SOCMINT also reveals the connections between people and groups. If one person is identified as a potential threat, social network mapping can reveal their connections. This can alert security agencies to individuals not yet on their radar.
During an active terrorism incident or threat, social media provides real-time, geolocated insights. These often include associated visuals, showing what’s actually happening on the ground.
Cyber defense and digital threat analysis
SOCMINT can help cybersecurity agencies identify emerging digital threats and attacks. SOCMINT tools with social media monitoring alerts can flag proof-of-hack content and other claims of responsibility for hacks. Tracking relevant keywords and hashtags can also help agencies spot upcoming hacking operations while they are still in the early stages.
Monitoring sentiment towards specific agencies and sectors can be another way to identify emerging digital threats. A significant shift in negative sentiment could indicate heightened risk of hacker intent.
Just as social network mapping can be useful for counterterrorism, it can work for cyber defence. In particular, mapping public connections between social accounts can give agencies a more nuanced understanding of hacker networks and threat actors.
Scam prevention and consumer protection
SOCMINT can help government and law enforcement agencies spot emerging scams and identify fraudulent accounts. Especially those impersonating government actors.
In 2024, consumers reported $16.6 billion in losses to digital crime, according to the FBI’s Internet Crime Complaint Center. IC3 received 17,367 complaints of government impersonation that same year. These alone led to more than $400 million in reported losses.
The U.S. public is currently not satisfied with the government’s response to cybercrime. Effective use of SOCMINT could help improve that perception.
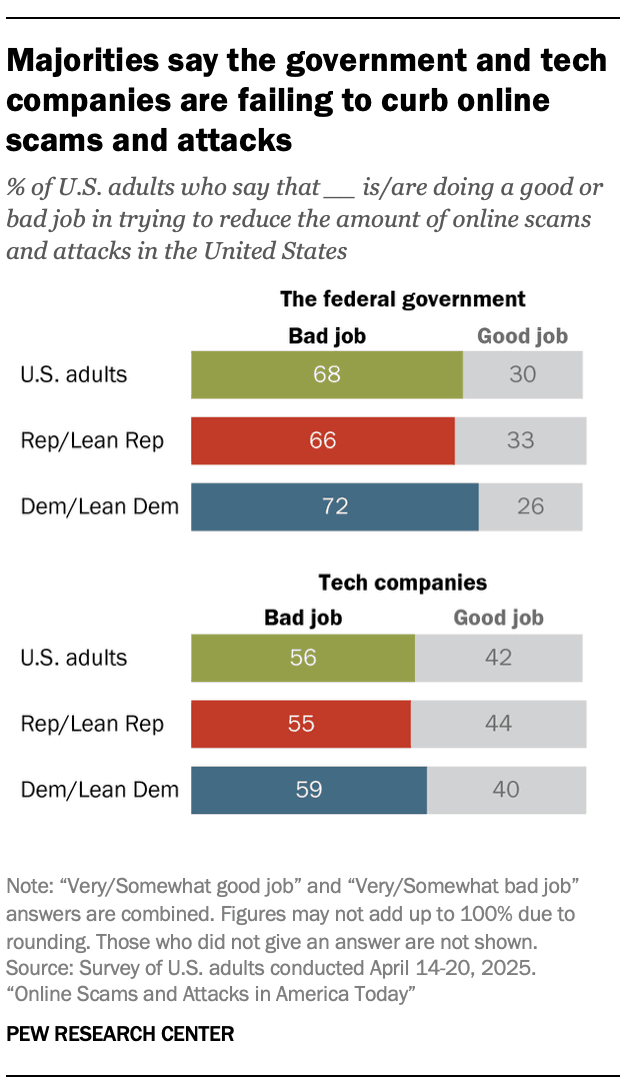
Source: Pew Research Center
Crisis response and situational awareness
Government agencies can’t have people on the ground everywhere, all the time. But they can gain real-time insights into what’s happening almost anywhere in the world at any moment. How? By analyzing geotagged social media content.
In a crisis, social media users may report what’s happening on the ground before traditional media outlets, support agencies, and often even law enforcement can arrive. Governments and law enforcement can use this content to see exactly what’s happening, often through photos and video.
SOCMINT also tells agencies how people on the ground are dealing with a crisis and what their immediate needs are. Good analysis of the data can help agencies plan everything from where rescue services are most urgently needed to what kind of public messaging is most useful.
Using aggregate data mapping, agencies can also track slower-moving emergencies. These may include disease outbreaks and public safety concerns.
Disinformation and influence operations
SOCMINT can help identify organized disinformation efforts and attempts to influence and manipulate public opinion. It’s particularly useful for identifying manipulation patterns, false narratives, and hashtag campaigns before they become accepted as truth.
Social network mapping is useful here, too. However, in this case, it’s often to see the links between bot social media accounts rather than between real people.
Mapping how global connection between conversations and topics can also reveal evolving disinformation campaigns. These may start with a grain of truth to gain credibility.
Once a disinformation campaign is underway, analyzing SOCMINT data helps agencies create effective counter-messages. They can be targeted to the right audiences on the platforms they use most.
How SOCMINT works: The intelligence cycle applied to social media
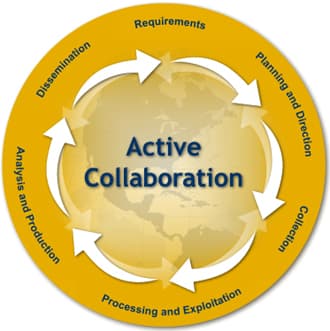
Source: FBI
The intelligence cycle is a process for gathering intelligence and using the findings to drive real policy decisions and actions.
The graphic above shows the FBI’s version of the intelligence cycle, which has six steps. Many agencies fold Requirements into the Planning and Direction stage. In that case, there are five stages rather than six.
Let’s look at how SOCMINT fits into this process.
Planning and Direction
Before you start gathering data, you need to be clear about what you want to learn and monitor. You also need to know why you want that information. How will the intelligence gathered benefit your organization or the public?
In the SOCMINT context, this is the stage where you will determine factors like:
Baseline levels of sentiment and activity: So you can watch for changes that may signal a threat
Which social platforms to focus on. You may want to start broad and narrow your focus once you start to see where the most relevant conversations are taking place.
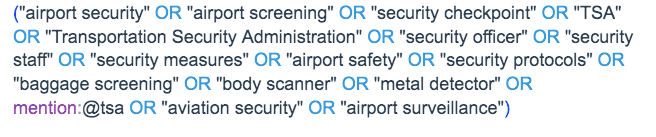
What topics, keywords and hashtags to monitor. An AI-powered query builder like the one built into Talkwalker can help.
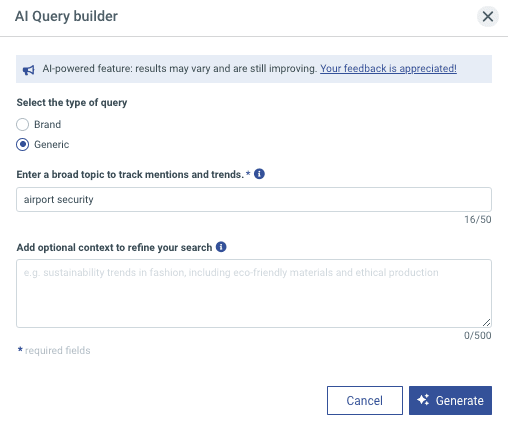
Resulting query generated by AI:
Collection
This is the data-collection and intelligence-gathering part of the process. Here, you can use a query like the one above to cast a wide net for social media conversion about a topic. You can also:
Monitor specific keywords and hashtags
Track mentions of specific accounts, groups, or people (both tagged and untagged)
Collect geolocation data
Set alerts to be notified immediately when data falls outside the anticipated parameters
Processing
SOCMINT can get messy. There’s a lot of noise to filter out. And the volume of data is so massive that it requires some structure for clear analysis.
Use advanced Boolean operators to reduce noise and false positives
Use AI tools (like Blue Silk AI in Talkwalker) for public sentiment analysis, image and video recognition, and language translation
Use SOCMINT tools like Talkwalker to summarize complex sets of unstructured data into dashboards, widgets, and clusters
Verify the authenticity of information and identify bots
Analysis
This is where data becomes intelligence. You can use your cleaned-up, structured, and summarized data to:
identify trends,
spot unusual changes in activity or sentiment,
and identify patterns of communication and behavior.
SOCMINT tools are critical at this stage. They can condense millions of data points into a clear chart or graph. They’re especially useful for spotting patterns and unusual activity.
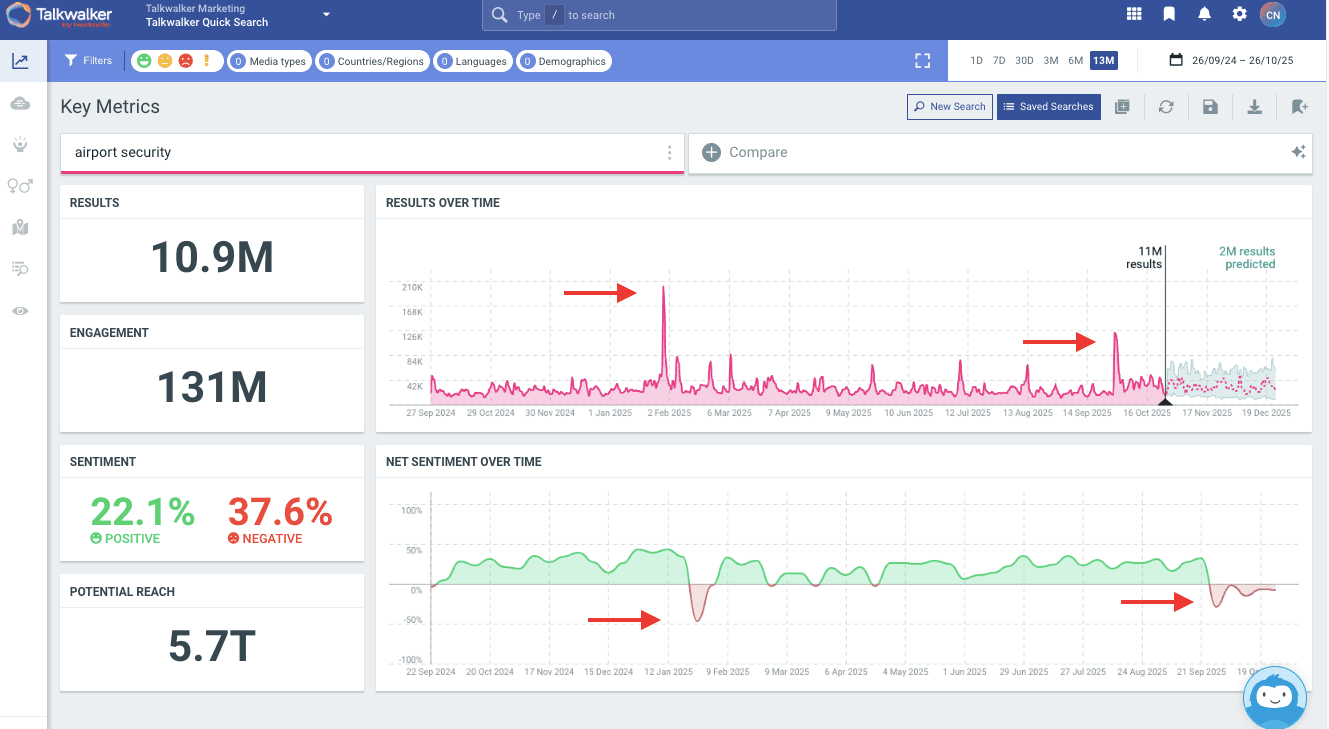
Dissemination
It’s time to share your findings with decision-makers. Again, SOCMINT tools are very helpful here. Tools like Talkwalker have built-in reporting capabilities and custom dashboards. These make it easy to summarize your findings, even for those outside the intelligence community.
This is also the stage in the intelligence cycle where new questions and priorities may emerge, and the process starts all over again.
Legal and ethical considerations
In this post, we’re talking only about using public data for SOCMINT investigations. Still, most jurisdictions have guardrails in place to protect reasonable expectations of privacy and data protection. The social platforms themselves also have terms of service that limit how their data can be used.
Here are some of the most relevant regulations to keep in mind.
General Data Protection Regulation (GDPR): European Union
This regulation applies to any organization processing the personal data of people in the EU or EEA. It applies equally across jurisdictions. The determining factor is where the people are whose data is being collected, not the location of the people doing the collecting.
The most important element of GDPR for SOCMINT is that consent is required to collect personal data. That includes public data. A person’s name and photo are still considered personal, even when they are part of a public social media profile.
Law enforcement and national security may fall under exemptions. But they are still subject to limitations and oversight.
California Consumer Privacy Act (CCPA): California
This law has some overlap with the GDPR. Like the GDPR, it requires knowledge of personal data collection. Both regulations also require that people know why their data is being collected. CCPA mainly regulates commercial use, so government agencies may be exempt.
Personal Information Protection and Electronic Documents Act (PIPEDA): Canada
Again, this law limits the use of personal data. It requires that individuals provide consent for data collection, with knowledge about its use. Like CCPA, this law focuses on the private sector. Government agencies may be exempt.
Intelligence vs. surveillance
If you’re using aggregate big data sets, you’re generally safe from privacy concerns. When you collect data that’s more personal in nature, you may be straying into surveillance. This is a gray area that veers into covert territory, and may be subject to relevant oversight.
Public opinion towards social media surveillance is consistently negative. As of 2023, 71% of Americans were worried about how the government used data collected about them. And 15% specifically said they were very worried about law enforcement monitoring what they do online. That rises to 23% for Hispanic Americans.
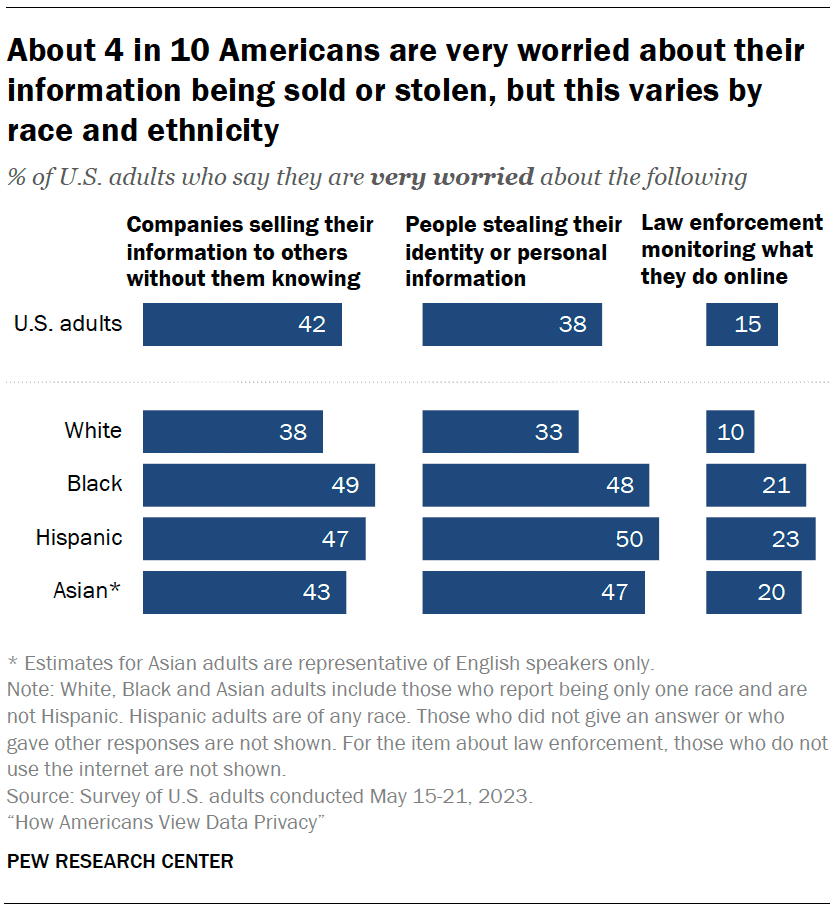
Source: Pew Research Center
The easiest way to stay compliant with relevant regulations and requirements (and maintain public goodwill) is to use compliant tools. Talkwalker and its parent company, Hootsuite, are both compliant with GDPR, CCPA, and PIPEDA. Learn more in the Hootsuite Trust Center.
Tools and technologies that enable SOCMINT
We’ve mentioned the importance of SOCMINT tools several times already. Here, let’s look at the different kinds of tools and technologies that make SOCMINT possible.
Social listening & analytics platforms
On this blog, we often talk about social listening as a marketing strategy. But the same tools that allow marketers to understand their audience are useful for intelligence agencies, defense analysts, and cybersecurity specialists. They can help you:
understand patterns,
track emerging threats,
monitor adversary activities,
gather situational awareness,
and more.
In Talkwalker, you can use Quick Search, alerts, and custom dashboards to monitor specific topics, hashtags, keywords, or accounts. This can be particularly useful when monitoring unfolding events or crises in real time.
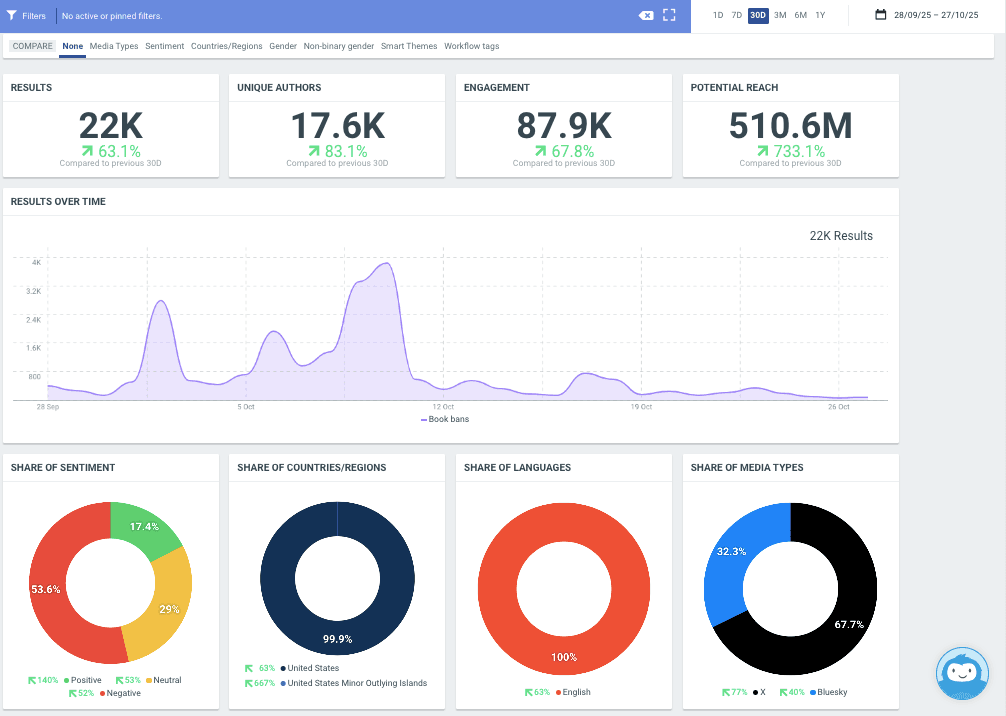
On the big data level, Talkwalker’s trend research and crisis monitoring features allow analysts to spot spikes in activity and sentiment. These may indicate disinformation campaigns, cyber attacks, real-world threats, and other coordinated activity. AI-powered sentiment analysis and anomaly detection automatically flag unusual patterns for follow-up. From there, you can use channel and topic analytics and conversation clusters to track how information is spreading and identify key actors and bots.
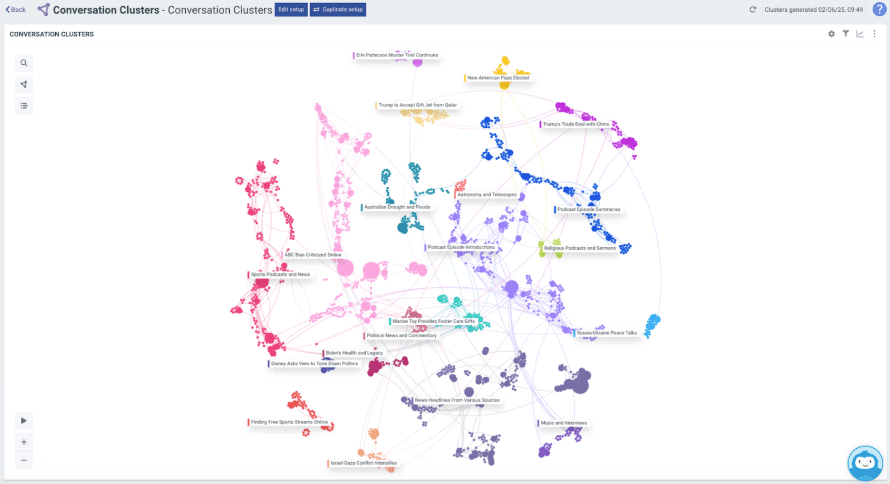
You can share information across teams and units within the Intelligence Hub. Once you reach the dissemination stage, you can create custom reports for each stakeholder group.
Network and entity mapping
We’ve mentioned social network mapping a couple of times. This is all about understanding the links between people, groups, hashtags, and causes. Then you can see how narratives spread among them. It can help identify key actors while allowing you to visualize how information flows and is amplified across the social web.
Understanding these connections and information pathways is especially useful for identifying and tracking misinformation and disinformation. They can help you understand how a conspiracy grows from a rumor.
Maltego is an investigative tool that visualizes connections to simplify large data sets.
Palantir is a leading tool for visualizing structured intelligence networks based on fragmented social data.
Verification tools
AI, deepfakes, and other manipulated content is a real problem for SOCMINT practitioners. If you’re using specific images, videos, or claims posted on social to inform an investigation, you need to verify the contents are real. You also need to check that they're presented in the correct context (not recycled from old events).
InVID offers a platform designed to authenticate video. They offer a suite of tools, including a browser plug-in. It helps verify videos and images through metadata extraction, reverse image search, and keyframe analysis.
Bellingcat methods are open-source, manual research techniques developed by a collection of researchers, investigators, and journalists. They have an extensive toolkit that can help with verification.
AI/NLP systems for sentiment and intent analysis
Artificial intelligence and natural language processing combine to help parse the language of comments, captions, posts, and even images and emojis. The goal is to understand the meaning and emotion behind the content. They can also reveal the intent and motivation of content, including threats and spreading propaganda.
This helps intelligence agencies monitor the mood around a sensitive topic without having to examine and analyze every single post.
Talkwalker includes AI tools for sentiment and emotion analysis.
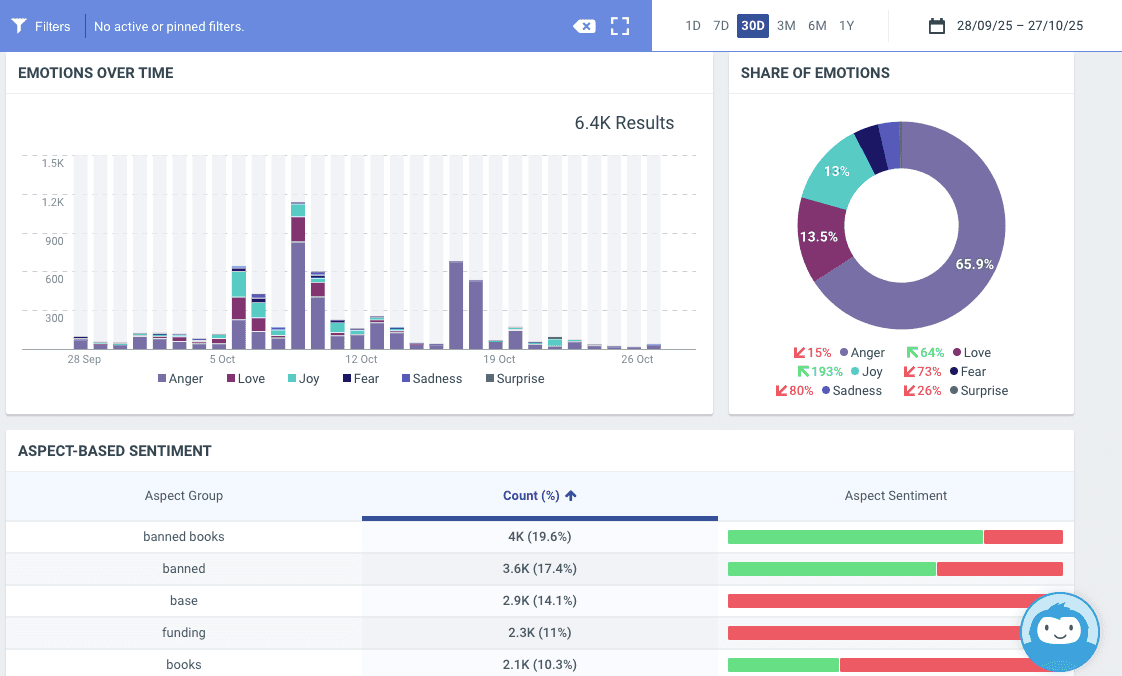
The future of SOCMINT: AI and multilinguality
Social media conversations happen across languages, regions and platforms. While we don’t have a specific figure of how many people are using languages other than English on social media, only about half of websites use English.
Social media, and the conversations that happen there are truly global and multilingual.
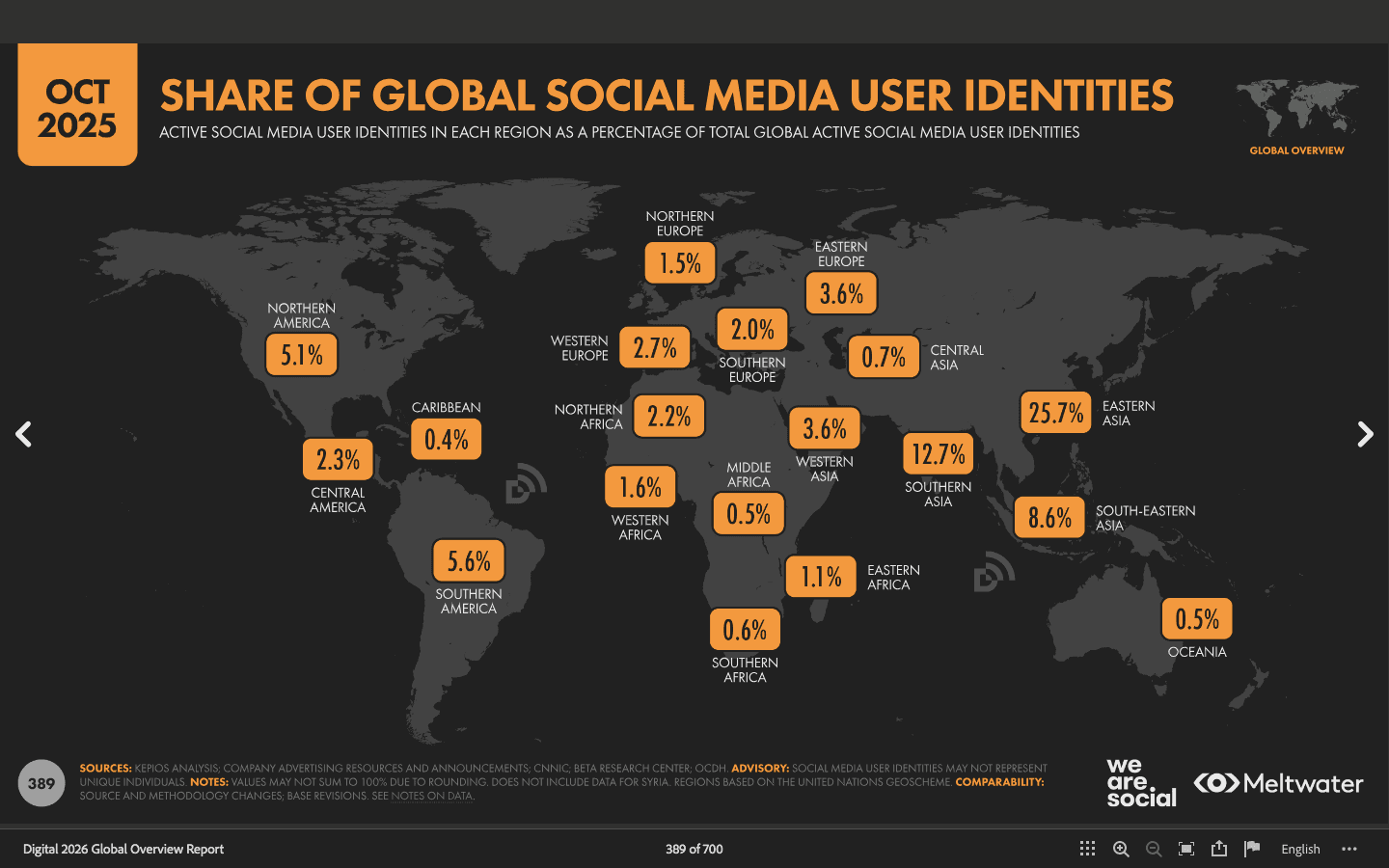
Source: Datareportal
AI tools with strong natural language processing capabilities are a critical tool for understanding sentiment, emotion, nuance, and connection in multilingual platforms. For example, Talkwalker crawls content from 239 countries and regions and can understand 187 languages.
It’s difficult to predict the future of AI tools when they are evolving so quickly. But we can certainly count on major AI developments for SOCMINT language processing. As their algorithms improve, AI tools will only get better at understanding cultural nuance across languages and regions. This will make SOCMINT an increasingly useful tool for global monitoring.
Want to turn public social data into actionable intelligence? Talkwalker’s SOCMINT capabilities help you detect emerging threats, track disinformation, analyze sentiment at scale, and gain real-time situational awareness across languages and regions—all while staying compliant with global privacy regulations. Book a Talkwalker demo to see how powerful social media intelligence can support security, cyber defense, and crisis response.
